Best-Selling Hosting
- Colocation Hosting
- Shared Hosting
- VPS Hosting
- Reseller Hosting
- Windows Hosting
- PHP Hosting
- Multiple Domain Hosting
- ASP Hosting
- Best Web Hosting Companies
- Dedicated Servers
- Java Hosting
- Managed Servers
- Coldfusion Hosting
- Linux Hosting
- Database Hosting
- > All Hosting Services
Top Rated Providers
Editors Pick
Detect and Clean a hacked server T0rnkit Tutorial
Published: Apr 22, 2004
-
Rating
5/5
Rating
5/5The complete guide to learn how to connect to your server using SSH. Simple to follow instructions with screenshots so anyone can follow along.
Getting started with SSH Tutorial - Connecting to your server with SSH
Secure Shell (SSH), sometimes known as Secure Socket Shell, is a UNIX-based command interface and protocol for securely getting access to a remote computer. It is widely used by network administrators to control Web and other kinds of servers remotely. SSH is actually a suite of three utilities - slogin, ssh, and scp - that are secure versions of the earlier UNIX utilities, rlogin, rsh, and rcp. SSH commands are encrypted and secure in several ways. Both ends of the client/server connection are authenticated using a digital certificate, and passwords are protected by being encrypted. SSH uses RSA public key cryptography for both connection and authentication. Encryption algorithms include Blowfish, DES, and IDEA. IDEA is the default.
The server you are connecting to must be running SSH, and you must be running a secure shell client on your own machine as well, more details on getting a secure shell client are below.
Step 1) Download the SSH client on your local machine, we are assuming you’re using Windows. If not then see other PuTTY download options here: http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html
Windows PuTTY Download
http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe
Step 2) Save the file to your desktop and double click it.
Step 3) You should see a something that looks like this, asking you what server you want to connect to.
Click for larger screenshot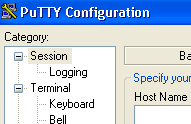
Step 4) Enter your servers IP and click on Open.
Step 5) Enter your account’s username to connect then enter your password.
Click for larger screenshot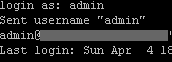
Step 6) Change to the root user, type: su –
That’s it! You have now logged into your server using SSH.
Now get comfortable with it and learn some shell/SSH commands in the article listed below.
Related Articles
- Guide to Chkrootkit - checking for intruders
- Creating a Welcome message for SSH logins
- Mask Your Web Server for Enhanced Security
- E-mail Alert on Root SSH Login
- How to install BFD (Brute Force Detection)
- How to install APF (Advanced Policy Firewall)
- How to install mod_security for Apache
- How to Disable Telnet
- How to install KISS Firewall
- Compile 2.6.7 Kernel w/module-init-tools
- Rkhunter Installation
Comments (3)
-
Steven Ciaburri 04:35, May 2, 2004PLease note run rkhunter you will find more items infected.
Thelinuxguy -
Jackson 09:33, October 23, 2005You should NEVER clean a rooted or comprimized system. <br />
<br />
You will never get all the files the hacker put in place on the server. You MUST and this is the ONLY way to make sure the hacker can not get back in to your system again is to either Format and reinstall or install a new drive and OS then salve the old drive over to the new and boot up... Mount the old drive and copy over your files... NO BINARIES THOUGH! Just user files.<br />
<br />
This has to be the stupidest tutorial ever. Any expert knows the only way to clean a rooted system is to start from scratch.<br />
<br />
Period. -
Kevin 23:47, January 18, 2006I agree with you Jackson. It's like dropping a cake on a wet, dirty floor. If you just give it a simple wipe on 1/4 of the cake. It's still dirty, but not as visably. Who knows? The hacker could have been smart and installed a few more root kits incase you follow this.
Add Your Thoughts
WebHostGear.com is a hosting directory, not a web host.
Copyright © 1998-2024 WebHostGear.com